To close out National Cybersecurity Awareness Month, here are some steps federal agencies can take to protect their IT systems from cyber attacks and cybersecurity vulnerabilities using the Authorization to Operate (ATO) process.
An ATO demonstrates that a federal agency has gone through a federally approved, detailed process to protect an IT system from incidents such as cyberattacks, security breaches, malware, and phishing attempts. Many federal IT systems are required to obtain an ATO to process government data and federal regulations recommend that agencies follow the Risk Management Framework (RMF) to become authorized.
GSA’s Highly Adaptive Cybersecurity Services (HACS) Special Item Number (SIN) provides solutions for all of an agency’s cybersecurity service needs, including RMF. The HACS SIN connects agencies with vendors who have passed oral technical evaluations for cybersecurity services performed within the RMF, and who are ready to assist agencies with the RMF process for a successful authorization.
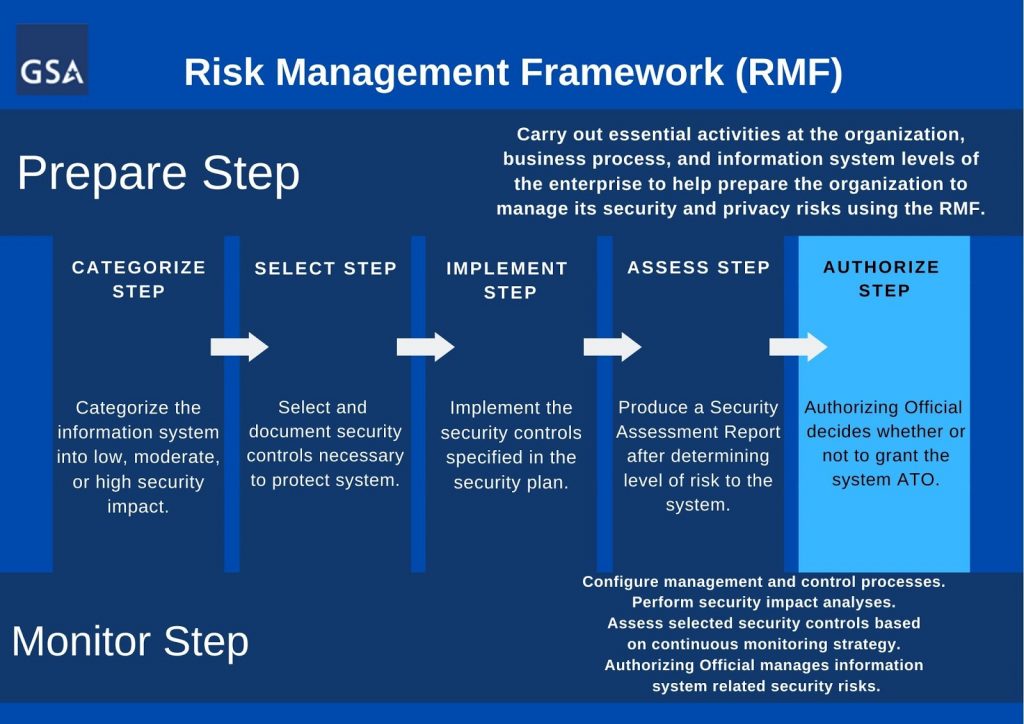
All of the steps, tasks, and activities that precede the “Authorize” step of the RMF help to prepare the information system for the authorizing official’s appraisal. The authorizing official is not a contractor, but a federal employee of whichever agency is seeking ATO.
The HACS SIN connects federal agencies with contractors who can help in each stage of the RMF. Contractors can assist agencies in producing the deliverables associated with each RMF step listed in the chart below.
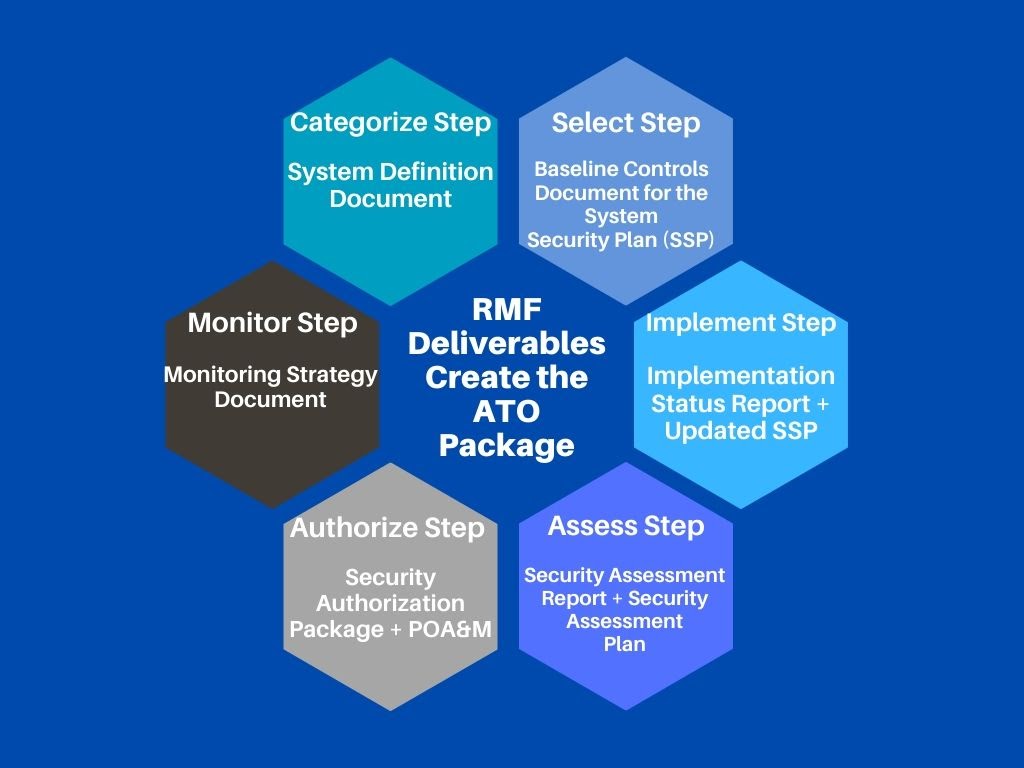
Once an agency has successfully completed the first four steps of the RMF (“Categorize” through “Assess”), an authorizing official will evaluate the system. The authorizing official for the federal agency in question evaluates residual risks identified during the security control assessment, and makes the decision to authorize the system to operate, deny its operation, or ask the agency to address any issues.
When granting an ATO, authorizing officials look for the following checklist of items:
- Plan of Action and Milestones (POA&M)
- Authorization Package
- Final Risk Determination and Risk Acceptance
- Authorization Decision
The POA&M is one of the most important deliverables produced in the RMF process. It reflects organizational priorities for addressing any remaining weaknesses and deficiencies in an information system and its environment of operation. The Authorization Package includes all key documents including the security plan, security assessment report, and the POA&M.
Following the RMF steps helps your agency to achieve ATO, but the work does not end after an ATO is issued. Agencies must also continuously monitor their systems to ensure that security controls remain effective over time.
In addition, many federal agencies must reauthorize their information systems every three years by going through the RMF process again. This is where the final step of the RMF, “Monitor Controls,” is important. As part of continuous monitoring, a sample of the applicable security controls are tested annually, periodic vulnerability scanning is performed, and security impact analysis of changes are performed. If an agency continuously monitors its systems over those three years by documenting specific technical changes, environment changes, or changes to the organizational risk management strategy, it may be easier to renew an ATO because any security risks can be mitigated at the time they occur.
For more information on HACS RMF services and how using the HACS SIN can make it easier for your agency to achieve an ATO, visit the HACS homepage or download the customizable RMF Statement of Work (SOW).
Please follow us on Twitter @GSA_ITC and LinkedIn to join our ongoing conversations about government IT.
To get updates for this blog, please sign up on the right-hand side of the page where it says Sign up for Blog Updates.