Continuous monitoring of IT systems is an evolving process. It adapts as new technologies and capabilities become available and as organizations are faced with advanced and persistent threats. However, the core strategies of continuous monitoring lay the foundation for safe and secured federal IT systems.
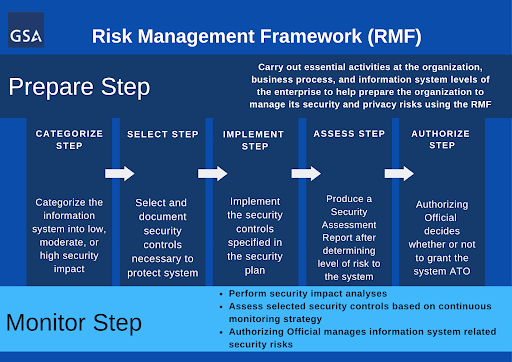
Continuous monitoring helps agencies identify, resolve, and understand key insights regarding certain risks to their information systems. The Risk Management Framework (RMF) process consists of several steps that include preparing a system for authorization, authorizing the system, and continuously monitoring the system until the next authorization process begins. The monitoring step is essential for agencies that want to minimize risks to their security systems.
As mentioned in previous posts, the Highly Adaptive Cybersecurity Services (HACS) Special Item Number (SIN) solution is available for agencies in need of cybersecurity services, including RMF. GSA’s HACS solution connects agencies with vendors who have passed an oral technical evaluation for cybersecurity services, making it easier for agencies to find quality vendors to assist with continuous monitoring strategies and Security Operations Centers (SOCs) activities.
After agencies obtain Authorization to Operate (ATO), they move into the continuous monitoring step of the RMF process. Though continuous monitoring strategies can vary by agency, usual tasks include near real-time risk management and ongoing authorization based on the system environment of operation. This step’s dynamic processes determine if a system’s security controls continue to be effective over time.
RMF services are available through GSA’s HACS SIN. A Statement of Work (SOW) for the RMF process can be found on the HACS website and includes example language for procuring services for the Monitor Step. The SOW outlines several subtasks that make up the continuous monitoring phase of RMF.
Roles and Responsibilities within the Continuous Monitoring Strategy
As part of the continuous monitoring process, the agency will oversee information system and environment changes. This process involves determining the security impact of proposed or actual changes to the information system and its environment of operation.
Security Control Assessments
An Information Owner (IO), Security Control Assessor (SCA), Information System Security Officer (ISSO), and Information System Security Engineer (ISSE) will be responsible for ongoing security control assessments. The IO is an inherently governmental position; however, contractors can provide support for the other roles in most situations. In these assessments, personnel examine the technical, management, and operational security controls within an information system. This practice ensures that a system is in accordance with the agency’s monitoring strategy.
Risk Determination
The Chief Information Security Officer (CISO) performs ongoing risk determination and acceptance as a part of continuous monitoring. This task consists of reviewing the reported security status of the information system (including the effectiveness of security controls employed within, and inherited by, the system) on an ongoing basis. The CISO aims to determine whether the risk to the agency’s system remains acceptable. If a risk is not acceptable, remediation will take place. This CISO is in an inherently governmental position; however, contractors can provide subject matter expertise and recommendations for risk determinations.
Ongoing Remediation
The IO and ISSO take part in ongoing remediation actions throughout the continuous monitoring process. Along with the Information System Owner (ISO) and the Common Control Provider (CCP), these personnel conduct remediation actions based on the results of ongoing monitoring activities, the assessment of risk, and outstanding items in the Plan of Action and Milestones.
For more information on HACS RMF services and how using the HACS SIN can make it easier for your agency to monitor its systems, visit the HACS homepage or download the customizable RMF Statement of Work (SOW).
Please follow us on Twitter @GSA_ITC and LinkedIn to join our ongoing conversations about government IT.
To get updates for this blog, please sign up on the right-hand side of the page where it says Sign up for Blog Updates.