What is Zero Trust Architecture (ZTA)?
Zero Trust is not a technology, but an approach to cybersecurity. It assumes all cyber networks and traffic are hostile in nature, and that any implicit trust in users should be eliminated. Now, more than ever, Zero Trust concepts are becoming increasingly important to an agency’s IT security posture as we see an increase in cyber attacks.
Zero Trust Architecture (ZTA) is a cybersecurity strategy that employs narrow and dynamic network defenses where every action, and use of resources is questioned, and where users are given the minimum levels of access to information needed to do their jobs.
To fully implement ZTA, organizations need to focus on the integration and implementation of a range of tactics and technologies. We can no longer rely on the concept of “trust, but verify”. Instead, agencies must verify, re-verify, and continue re-verifying with added layers of cybersecurity to establish true ZTA.
Why is ZTA important now?
Recent sophisticated cyber attacks and the shift to remote/virtual work environments highlight the importance of focusing on cybersecurity. The recent Sunburst and Colonial Pipeline cyber attacks exposed vulnerabilities in government and private sector computer systems. These attacks are a stark reminder that a weakness anywhere is a weakness everywhere. Furthermore, as organizations move to a mix of cloud-based, on-premises, and hybrid network models, traditional perimeter-focused network defenses can no longer protect an organization’s information communication technology assets. To keep pace with today’s dynamic and increasingly sophisticated cyber threat environment, government agencies must move quickly to modernize their cybersecurity capabilities and accelerate towards the adoption of ZTA.
In 2020, the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207, Zero Trust Architecture was released to provide agencies with guidance and detailed recommendations to improve their security posture using the core principles of ZTA. More recently, Executive Order 14028 “Improving the Nation’s Cybersecurity” requires all Federal agencies to develop a plan to implement ZTA in an effort to modernize and strengthen cybersecurity standards and detection.
What can agencies do to embrace ZTA?
Although there is no single end-to-end, comprehensive Zero Trust network solution, movement towards a Zero Trust security posture does not require agencies to rip and replace existing cybersecurity tools, hardware, or software products. Rather, agencies can make incremental steps to “re-tool” existing products to adhere to Zero Trust principles and supplement with GSA-offered products, services, and solutions to achieve ZTA.
GSA created a Zero Trust Architecture Buyer’s Guide for acquisition, network architect, and cybersecurity professionals who are seeking to implement ZTA. The guide is a roadmap to ZTA and provides helpful concepts and best practices. Zero Trust security models currently range between five and seven pillars. For the purposes of facilitating an acquisition-based perspective, GSA chose to represent a combination of eight unique pillars that agencies should consider when implementing a robust and efficient Zero Trust security model.
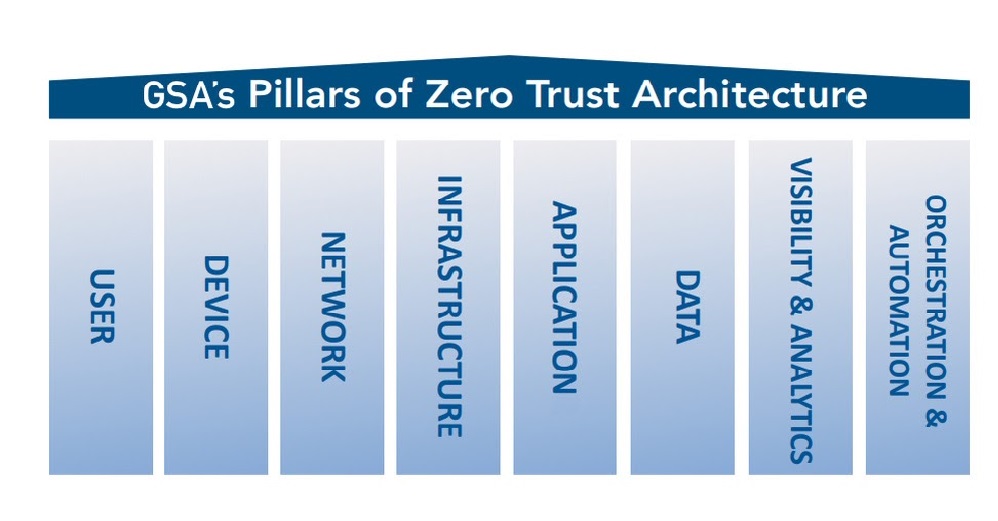
Getting to Zero Trust is a journey. Moving to ZTA will take time, and agencies will be at different starting points as they implement a Zero Trust strategy. When evaluating a ZTA solution, agencies should consider how well the product or service addresses these eight pillars and to what extent.
Zero Trust Pillars
| Pillar | Description |
| User | Involves focus on user identification, authentication, and access control policies which verify user attempts connecting to the network using dynamic and contextual data analysis. |
| Device | Performs “system of record” validation of user-controlled and autonomous devices to determine acceptable cybersecurity posture and trustworthiness. |
| Network | Isolates sensitive resources from being accessed by unauthorized people or things by dynamically defining network access, deploying micro-segmentation techniques, and control network flows while encrypting end-to-end traffic. |
| Infrastructure | Ensures systems and services within a workload are protected against unintended and unauthorized access, and potential vulnerabilities. |
| Application | Integrates user, device, and data components to secure access at the application layer. Security wraps each workload and compute container to prevent data collection, unauthorized access or tampering with sensitive applications and services. |
| Data | Involves focus on securing and enforcing access to data based on the data’s categorization and classification to isolate the data from everyone except those that need access. |
| Visibility and Analytics | Provides insight into user and system behavior analytics by observing real-time communications between all Zero Trust components. |
| Orchestration and Automation | Automates security and network operational processes across the ZTA by orchestrating functions between similar and disparate security systems and applications. |
How can GSA help?
There are many elements of a Zero Trust solution that crosscut and incorporate GSA contract offerings. The information provided in the Zero Trust Architecture Buyer’s Guide can help agencies mature their Zero Trust implementation plans.
There are multiple GSA resources that support Zero Trust efforts, like the Highly Adaptive Cybersecurity Services (HACS) Special Item Number (SIN) which provides access to vendors who have passed an oral technical evaluation for cybersecurity services, making it easier for agencies to find quality vendors.
The Continuous Diagnostics and Mitigation (CDM) Tools SIN provides access to cybersecurity products included on the Department of Homeland Security Cybersecurity & Infrastructure Security Agency’s Approved Products List. Agencies can use these and other comprehensive GSA solutions to support the design and deployment of architectures that follow the tenets of Zero Trust.