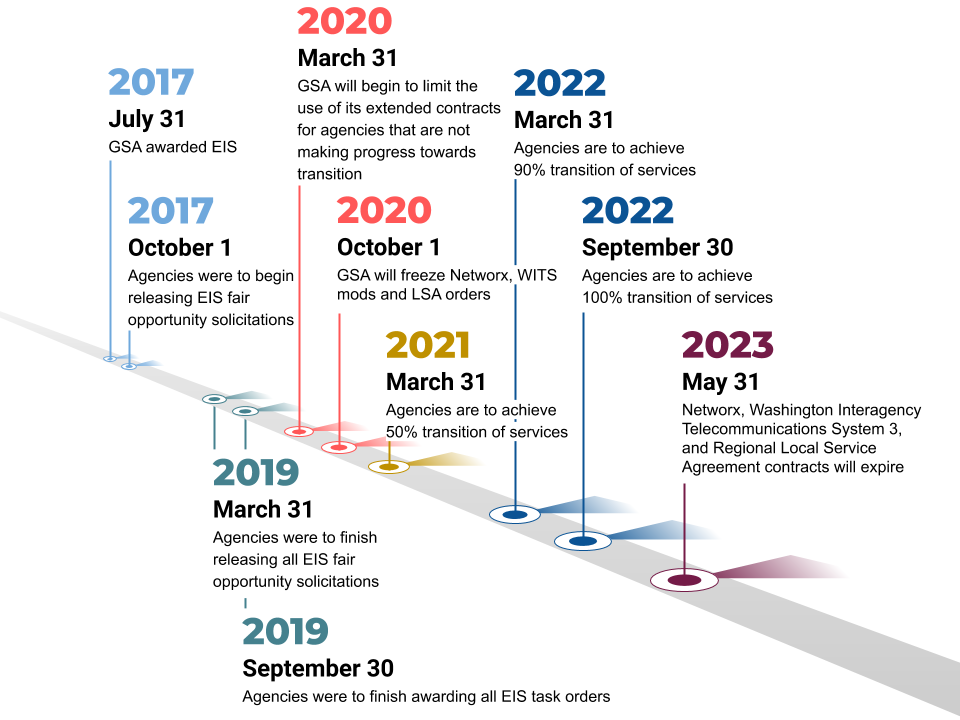
Timeline of the Planned Transition to Enterprise Infrastructure Solutions
In December 2018, GSA announced that we would extend the expiring Networx, Washington Interagency Telecommunications System (WITS) 3, and Regional Local Service Agreement (LSA) contracts to allow the necessary time for agencies to complete transition and modernize.
The successful transition to Enterprise Infrastructure Solutions (EIS), the federal government’s $50 billion, 15-year, Best-in-Class acquisition vehicle for telecommunications and networking, is a strategic priority for GSA’s Federal Acquisition Service.
Originally set to expire in 2020, GSA is extending the expiring contracts by an additional three years to May 2023. In extending these legacy contracts, GSA requires agencies to meet certain critical milestones to continue using services on the extended contracts.
Additionally, GSA is taking steps to curtail the growth of services on the extended contracts by freezing modifications and limiting use. These actions will minimize the impact of GSA having to maintain dual operations.
Freezing Modifications on Extended Contracts
Effective October 1, 2020, GSA will implement controls on its extended Networx, WITS 3, and LSA contracts by freezing all future growth on these vehicles. All new services should be provided under the EIS contracts.
Processing Modifications on EIS Contracts
GSA recognizes that many agencies have released their EIS solicitations and are waiting for EIS contract modifications to be evaluated and awarded by GSA. We are prioritizing modifications needed for agency awards.
Limiting Use of Extended Contracts
On March 31, 2020, GSA will begin to limit the use of its extended contracts for agencies that are not making progress towards transition. GSA will disconnect agencies, in phases, to meet the September 30, 2022 milestone for 100% completion of transition. The first phase will include agencies that have been “non-responsive” to transition outreach from GSA. Future phases will be based on each agency’s status at that time and the individual circumstances impacting that agency’s transition progress, such as protests or pending contract modifications.
Once a phase is complete, agencies identified will no longer be allowed to process any modifications or orders, will be ineligible for an exception, and will have their active services disconnected.
We applaud the agencies that are taking active steps to modernize and we will continue to monitor progress across the federal government. Taking steps to curtail growth on the extended contracts will encourage agencies to transition existing and new services onto EIS. GSA will continue to communicate with agencies at all levels, provide resources and support to agencies through transition, and pull all available levers in support of significant cost savings, greatly improved efficiencies, and enhanced cybersecurity— all achievable through EIS.
Questions? Contact Allen Hill, Executive Director, GSA’s Office of Telecommunications Services at allen.hill@gsa.gov or (202) 701-7891.
Please follow us on Twitter @GSA_ITC and LinkedIn to join our ongoing conversations about government IT.
To get updates for this blog, please sign up on the right-hand side of the page where it says Sign up for Blog Updates.


