At the beginning of every fiscal year, we sit down to develop our targets, and as I look back on the last year I’m very proud to see what we’ve been able to deliver for agencies.
Employee, customer, and industry input is key
Results of the Federal Employee Viewpoint Survey (FEVS), Customer Loyalty Satisfaction Survey (CLS), and the Industry Satisfaction Survey (ISS) are all part of a broader feedback ecosystem that drives our decisions. These three surveys collectively show a top-line level of ITC health and our progress in improving engagement and experience across ITC’s employees, customers, and suppliers.
This feedback is driving many of the decisions we make. At the end of the day, we’re here to serve, and so we look very closely at those survey results. I’m pleased that year over year, ITC customer loyalty and industry satisfaction remained steady, but I’m even more interested in what these surveys tell us about areas where we can improve.
Customers are telling us that ease of acquiring is the strongest driver of your loyalty and that you’d like to see us further improve internal processes, customer service, and communications generally.
Industry, on the other hand, said procurement process and industry expertise were your strongest drivers of satisfaction. You, too, would like to see improved processes and communications.
We hear you both and are working on ways to improve these concerns. There’s clearly some overlap here, and this gives us some clear direction.
If you’re a small business that’s new to the government market, it can be daunting. We’re working on solutions to make this all easier. One great example that we’re seeing is from the 8(a) STARS III GWAC where of the 258 industry partners who have task order awards, 149 of them received their first GSA contract vehicle task order award through 8(a) STARS III. Brand new to GSA contracting, and they’re already out the gate with orders.
This is great news, and we’re learning what we can from these results.
By the numbers
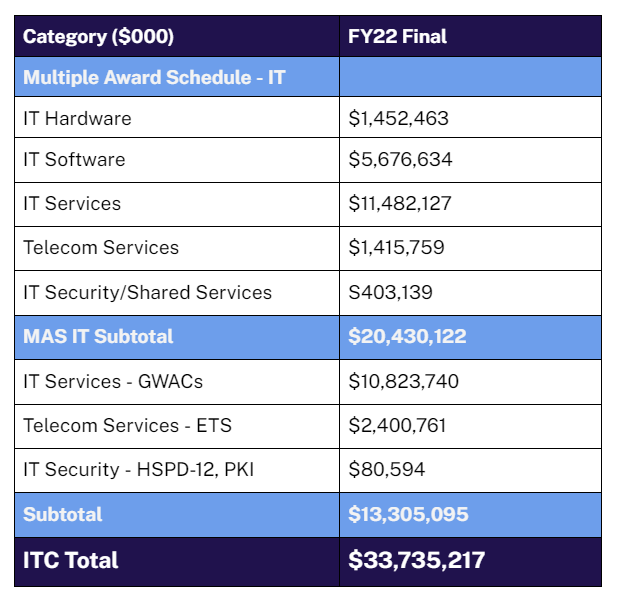
In every IT subcategory (Hardware, Software, IT Services, Telecom, and IT Security), we exceeded our FY22 targets.
IT Services on the Multiple Award Schedule had a particularly strong year surpassing our target by nearly 29 percent, with a year-over-year positive variance of more than 16 percent.
Mission spend through our IT contracts reached just shy of $34 billion for the first time and surpassed the previous year by nearly 5 percent. Volume over the last 4 years has increased by about $8.5 billion, which is truly remarkable. And most importantly, ITC helped agencies save nearly $2 billion through cost avoidance in the last year alone.
While we celebrate these successes, we’re also looking to the future for what’s next.
Trends, informing the future
Diversity, equity, inclusion, and accessibility initiatives are particularly important to the Biden-Harris Administration, and a big part of that is helping small businesses succeed in government contracting. I’m happy to report that ITC handily exceeded our small business utilization goals last year for small businesses generally, women-owned, services-disabled, and HUBZone small businesses. Small Disadvantaged Business performance was also very strong. Small businesses have won approximately $8.45 billion in FY22 (up 9.4 percent from $7.7 billion in FY21) through their work on ITC contracts.
We’ve been working hard on ways to make it easier for small businesses to support the government. We’re setting up Polaris, our next small business contract, and so I expect to see this trend of small business utilization continue.
In terms of the market, IT services are in high demand, and I would expect that to continue too. Automated Contact Center Solutions, Health IT, Cloud adoption, Earth Observation, and Highly Adaptive Cybersecurity Services were all particularly strong year over year.
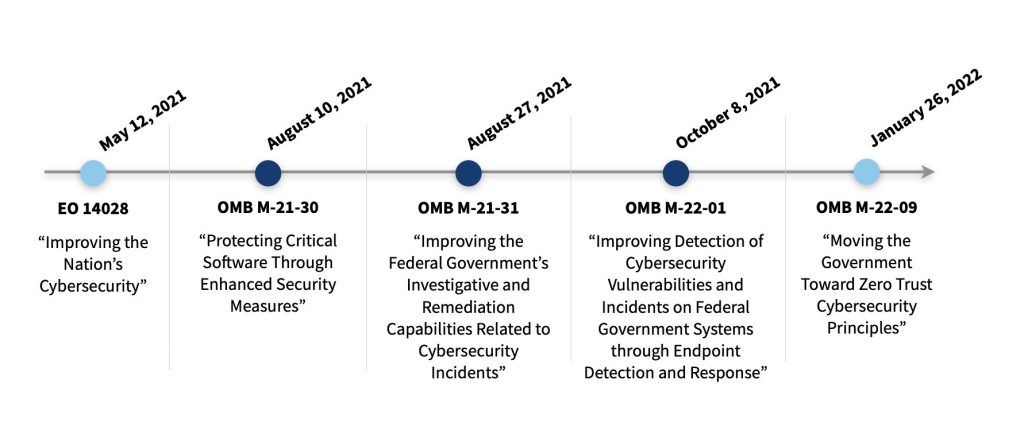
Speaking of cybersecurity, that’s another important topic to watch this year. We’re tracking trends and technologies that can help our customers improve their cybersecurity hygiene and strengthen their cybersecurity posture.
Looking forward, together
As we wrap up FY22 and kick off FY23, I want to thank our customers, industry partners, and ITC staff. It’s because of our close collaboration that we have these successes to celebrate.
Visit our website to learn more about our solutions, or use our IT Solutions Navigator to find the vehicle that’s right for you.
Follow ITC on Twitter and LinkedIn, and subscribe for blog updates.