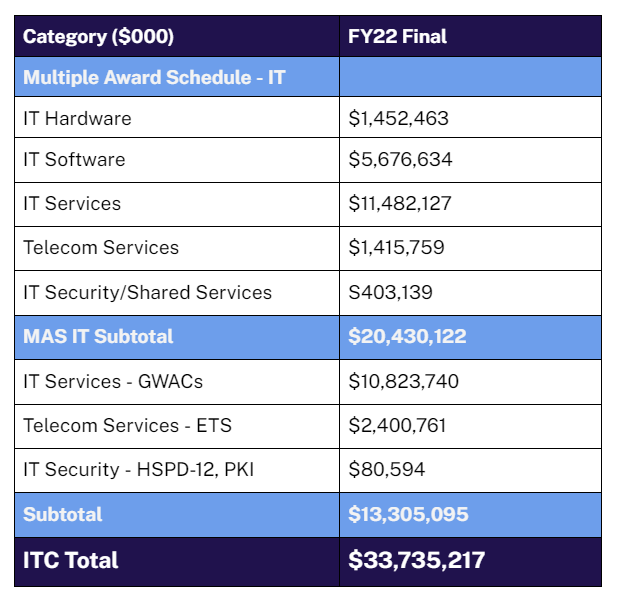
“Improving the Nation’s Cybersecurity” is a top priority across all federal agencies. Constant and fast-paced application innovation is the new norm of today’s digital enterprise. Vulnerabilities are waiting to be exploited by adversaries and their increasingly sophisticated malicious attempts such as the Log4J application exploitation.
The Office of Management and Budget’s (OMB) Memorandum 22-09 specifically charges agencies to operate dedicated Application Security Testing (AST) programs for a stronger and more robust cyber posture. Early and continuous AST minimizes the risk of sensitive data exposure and system compromise. To prevent most application security threats, agencies need a dedicated AST program that implements a variety of tools to continuously assess and address application vulnerabilities throughout the Security Development Life Cycle (SDLC).
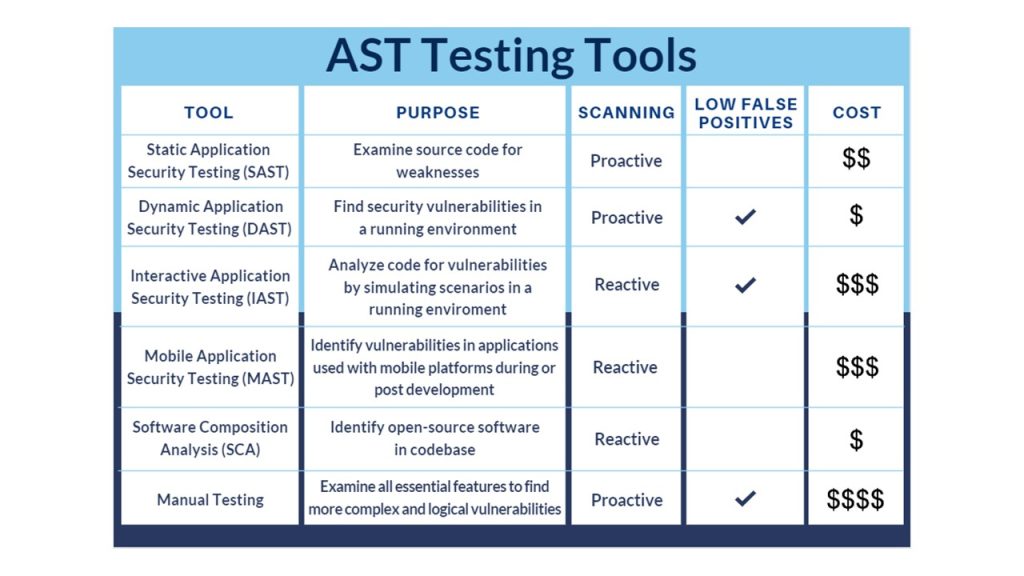
AST tools
Testing requirements and guidance released by OMB, the National Institute of Standards and Technology, and the Cybersecurity and Infrastructure Security Agency will make applications more resistant to security threats and identify security weaknesses and vulnerabilities. Ultimately, the goal is to create a holistic AST program of automated tools and manual testing that continuously examines applications as they are developed and continue through the SDLC. AST methodologies can be categorized into:
- Automated AST relies on written code/test scripts and tools to test and validate an application. It can be completed in less time than manual testing and covers more test permutations; however, it does require heavy coding and maintenance.
- Manual testing is executed by human security testers to discover complex bugs for which automated testing cannot detect or to resolve automated testing’s false positives. It requires a substantial level of expertise, effort, and time.
An AST program uses a variety of tools throughout the SDLC, many of which are described in the table below.
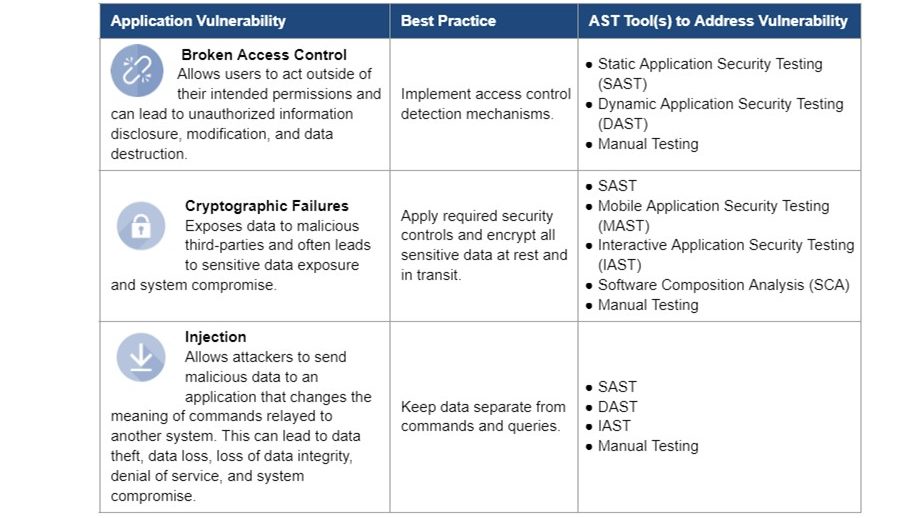
Top AST threats
According to the Open Web Application Security Project (OWASP), the top three application security threats are broken access control, cryptographic failures, and injection.
Third-party application security testers
Another component of a dedicated AST program is the use of independent third-party application security testers who specialize in identifying vulnerabilities internal staff may miss. These expert firms have the skills and certifications required to provide high-quality results and ensure applications hold up against real-world cyber attacks.
GSA cybersecurity resources
GSA created the AST Buyer’s Guide to help federal agencies meet AST program requirements, provide Third-Party Application Security Tester selection criteria, and address application security threats. It provides an overview of AST, key considerations when implementing an AST program, and helps identify and procure AST offerings to improve your agency’s application security posture.
To make the acquisition experience easier and more efficient, GSA also provides useful resources like an AST summary sheet, AST statement of work template, and AST informational video. These and many other resources can be found at www.gsa.gov/ast.
GSA cybersecurity support
The GSA IT category team is available to answer questions and provide subject matter expertise related to purchasing AST, cybersecurity, and a full range of IT products and services. Please contact the IT customer service center at 855-ITaid4U/855-482-4348 or itcsc@gsa.gov.
Follow ITC on LinkedIn and Twitter, and subscribe for blog updates.